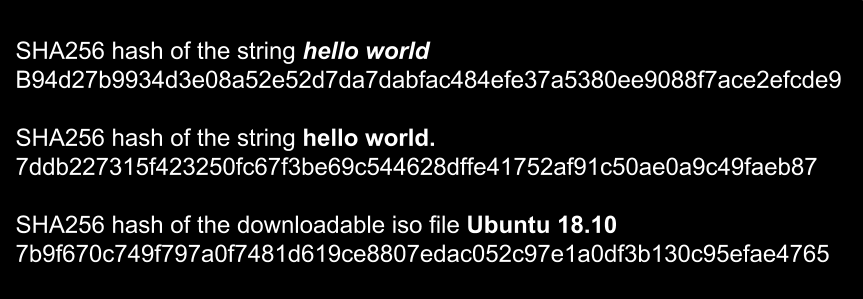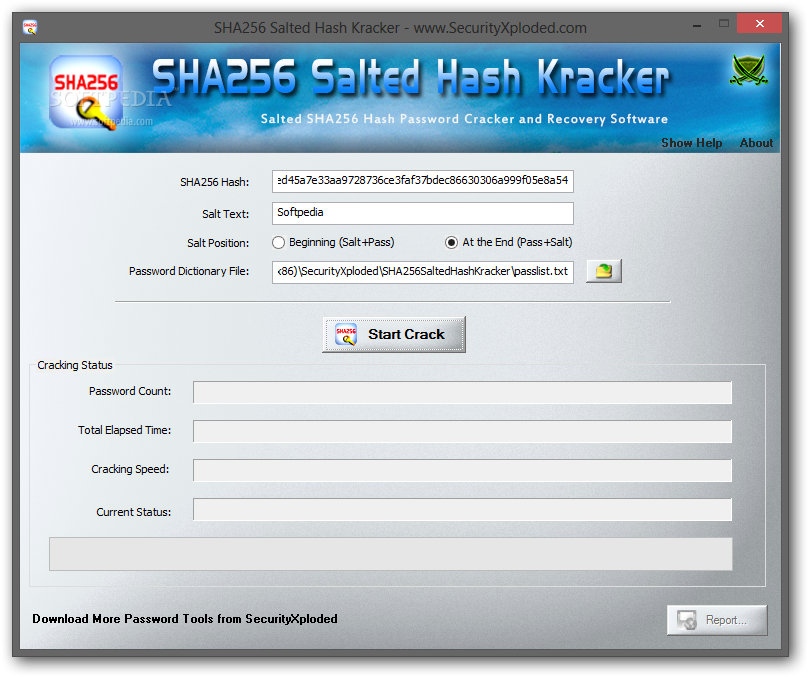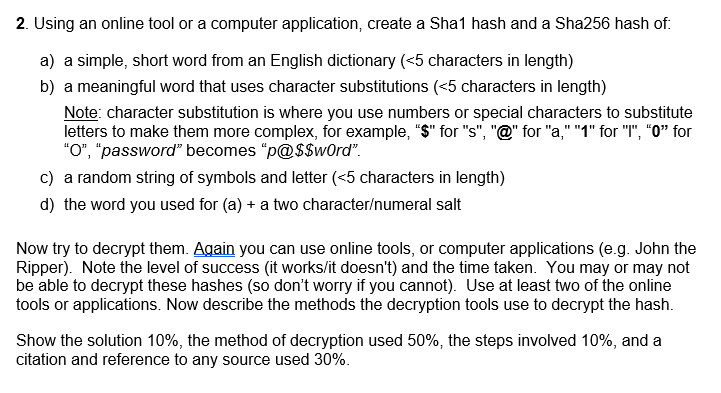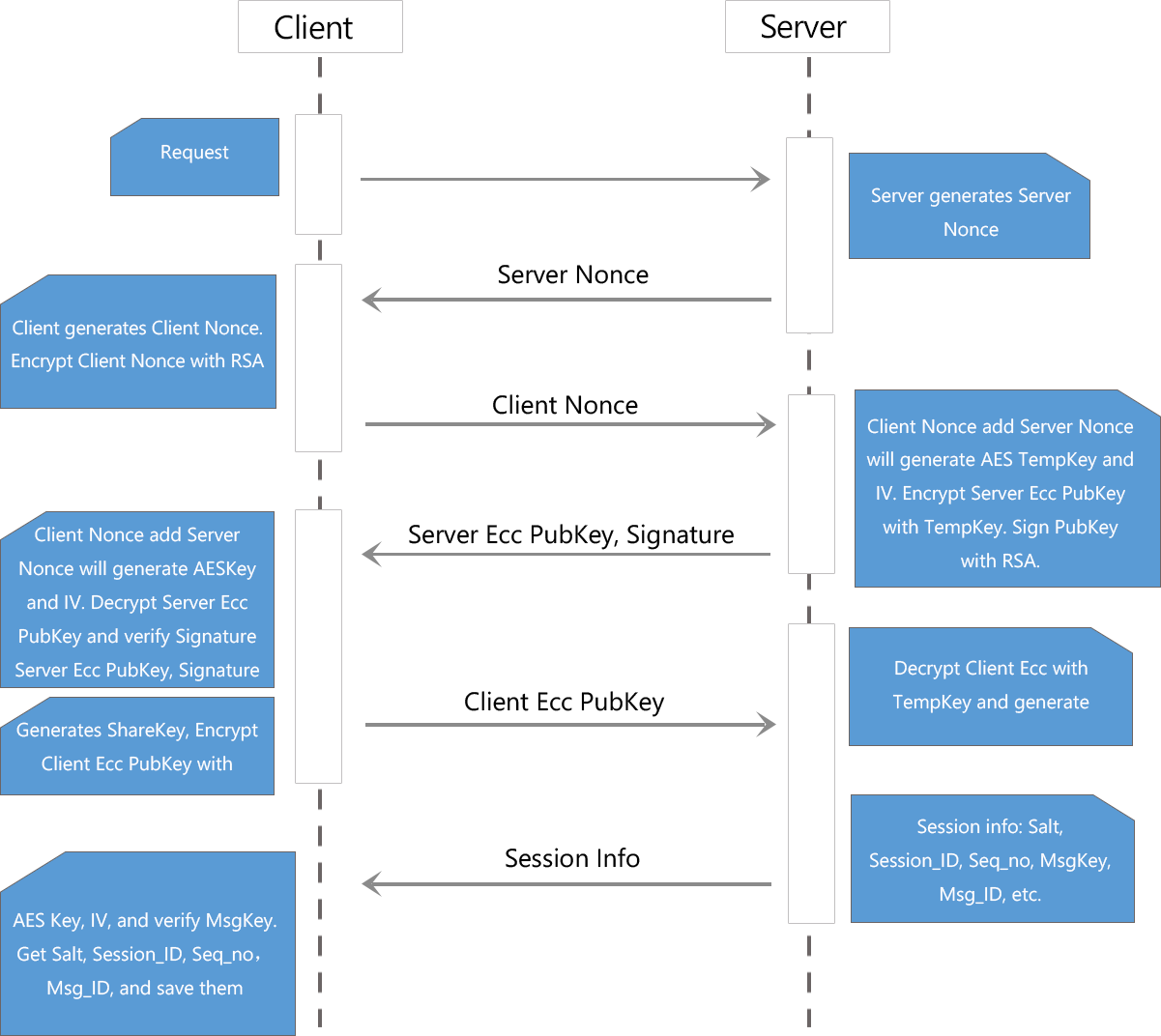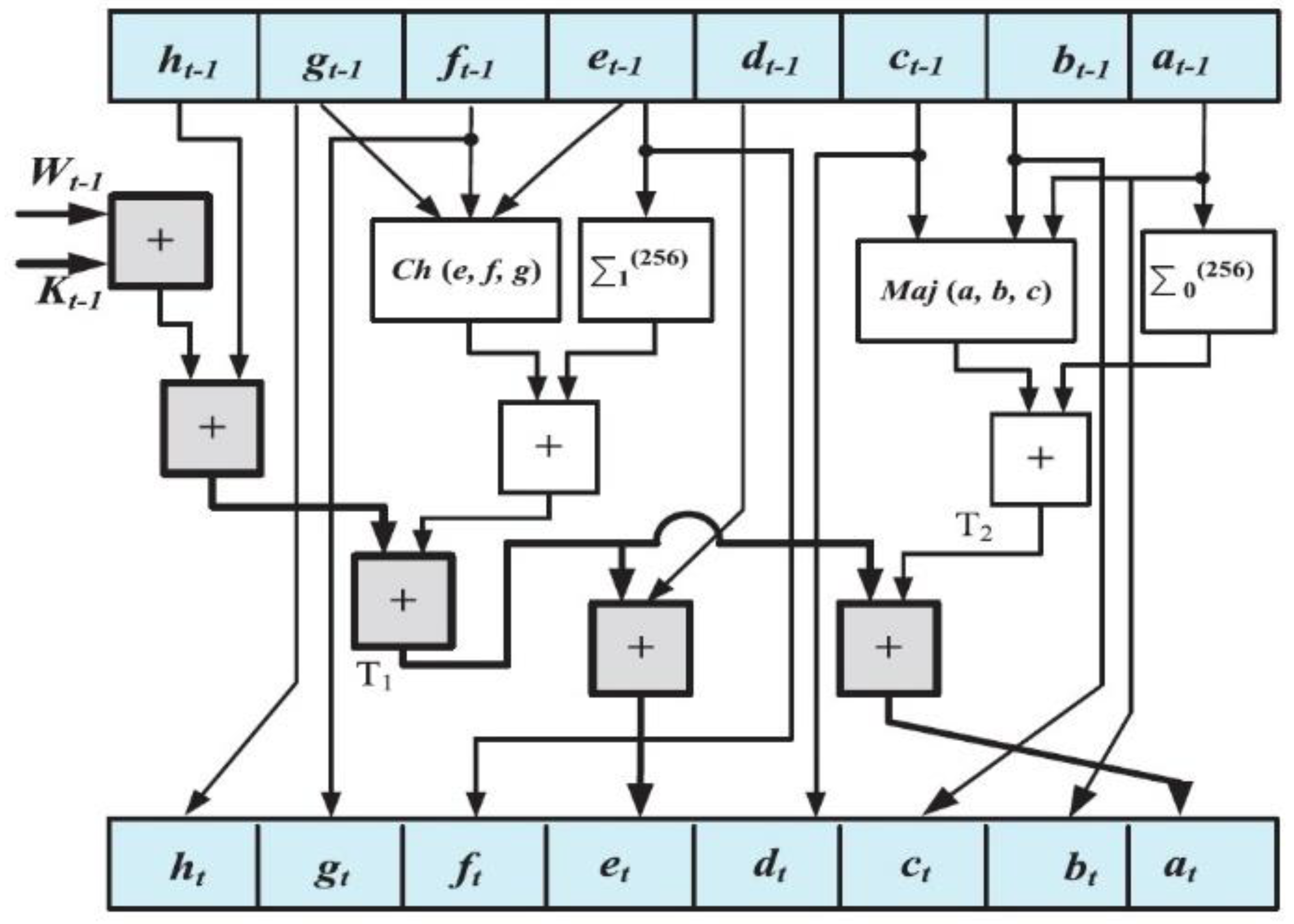
Entropy | Free Full-Text | A New Algorithm for Medical Color Images Encryption Using Chaotic Systems

Understanding Cryptography. Understand how encryption, decryption… | by Wei-Meng Lee | Level Up Coding

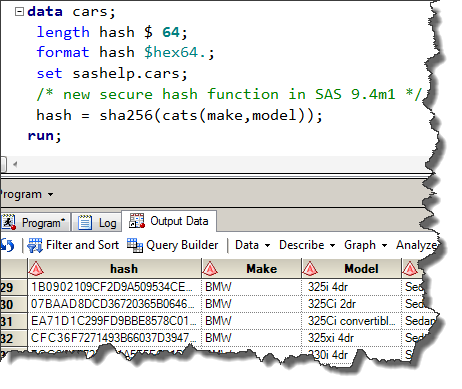
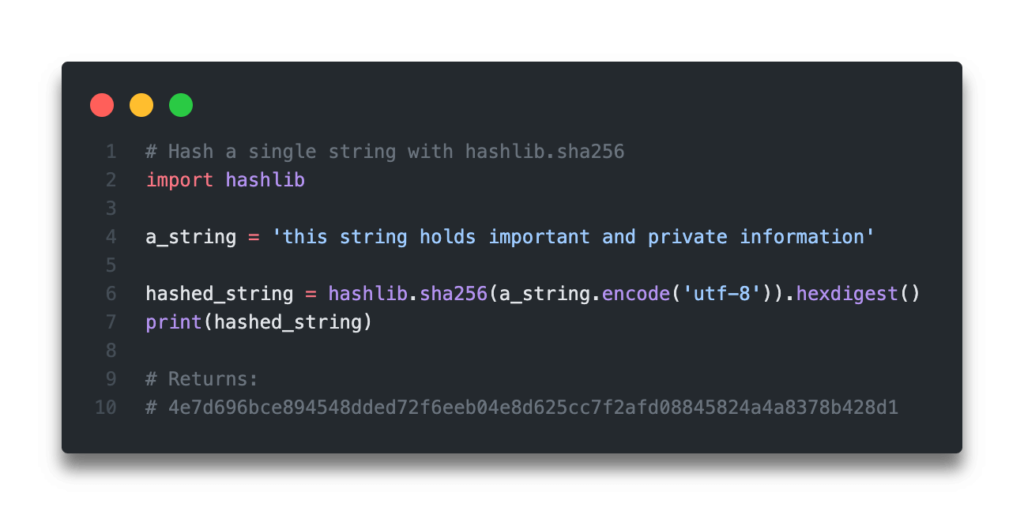
SHA 256: Compute a SHA 256 hash using C# for effective security - .Net Core | MVC | HTML Agility Pack | SQL | Technology Crowds
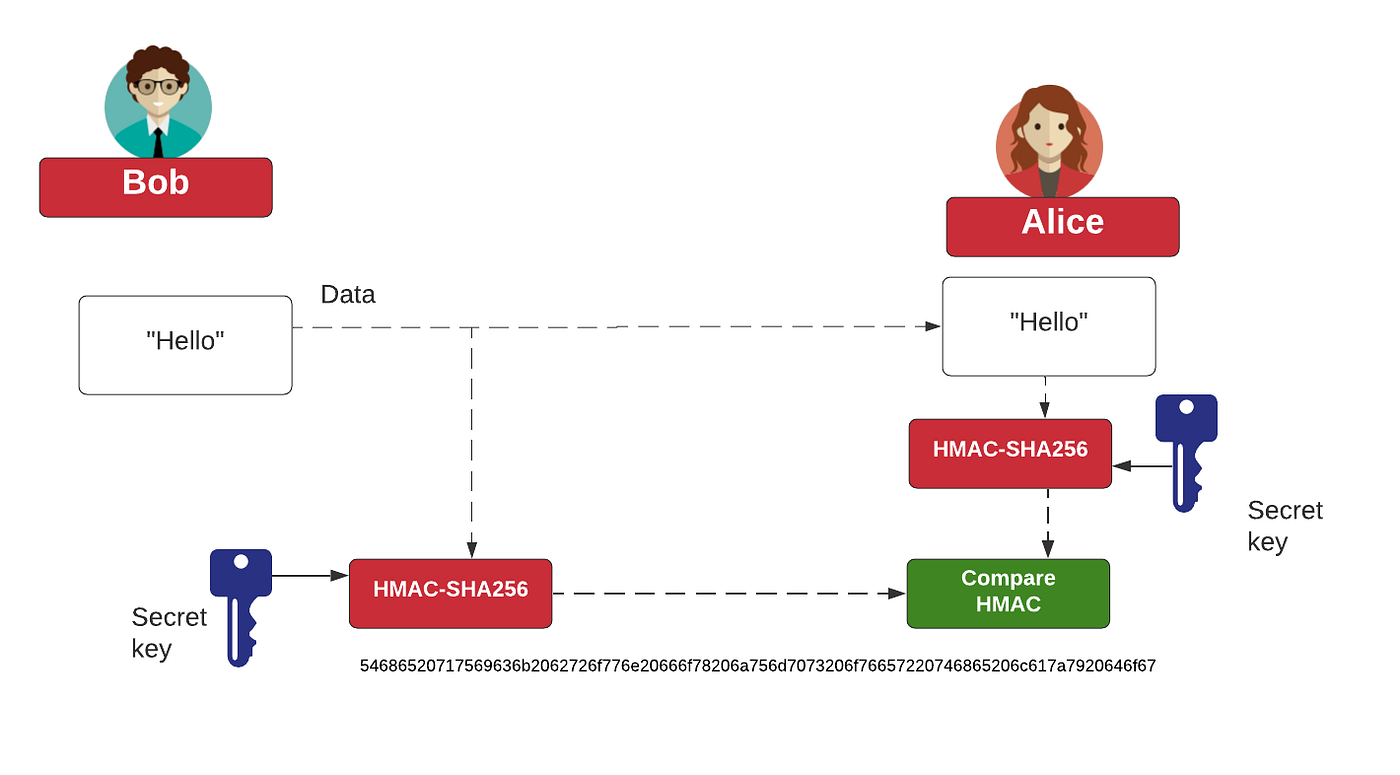
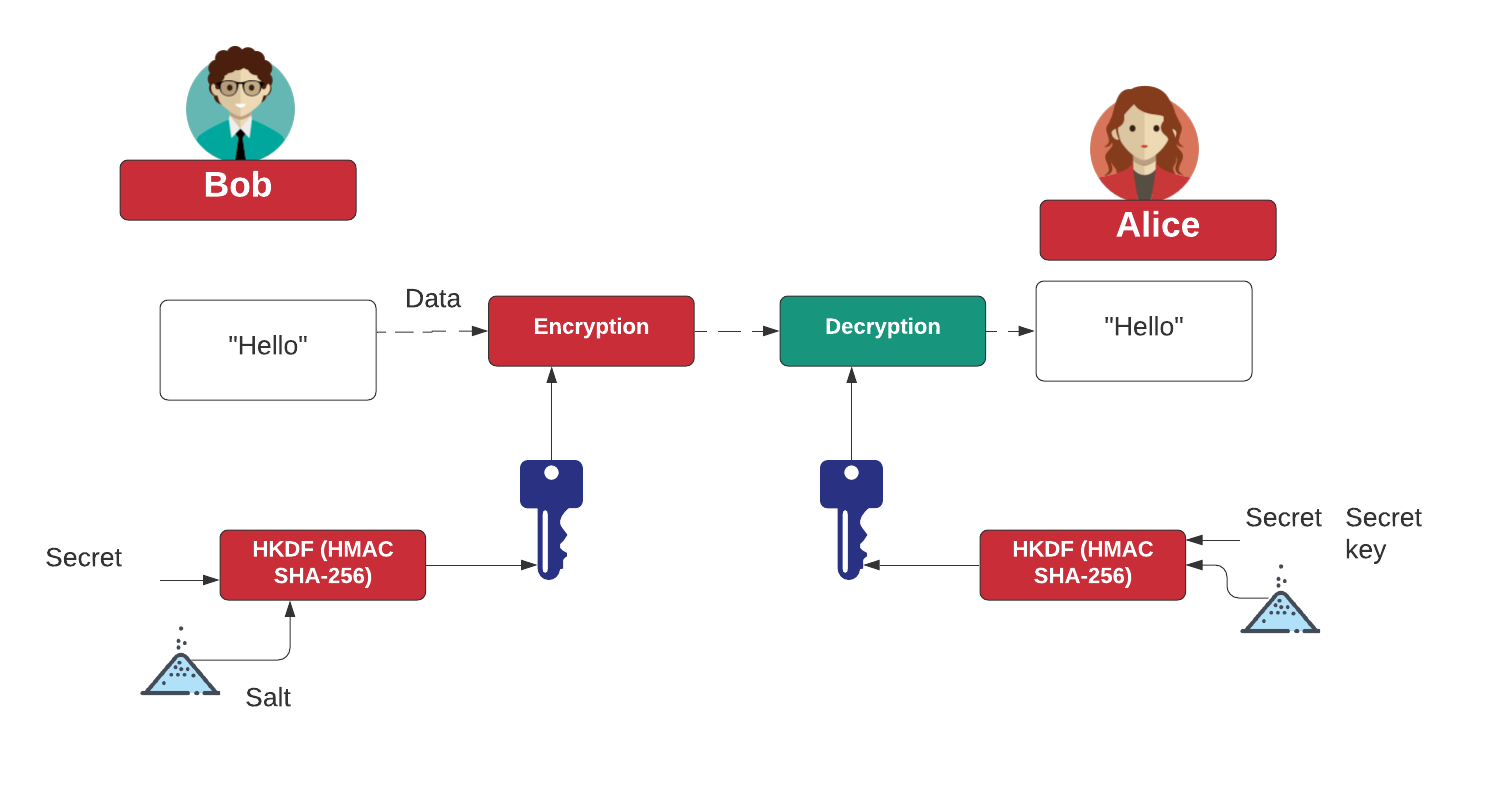
HMAC and HKDF. What's the right way to correct an… | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

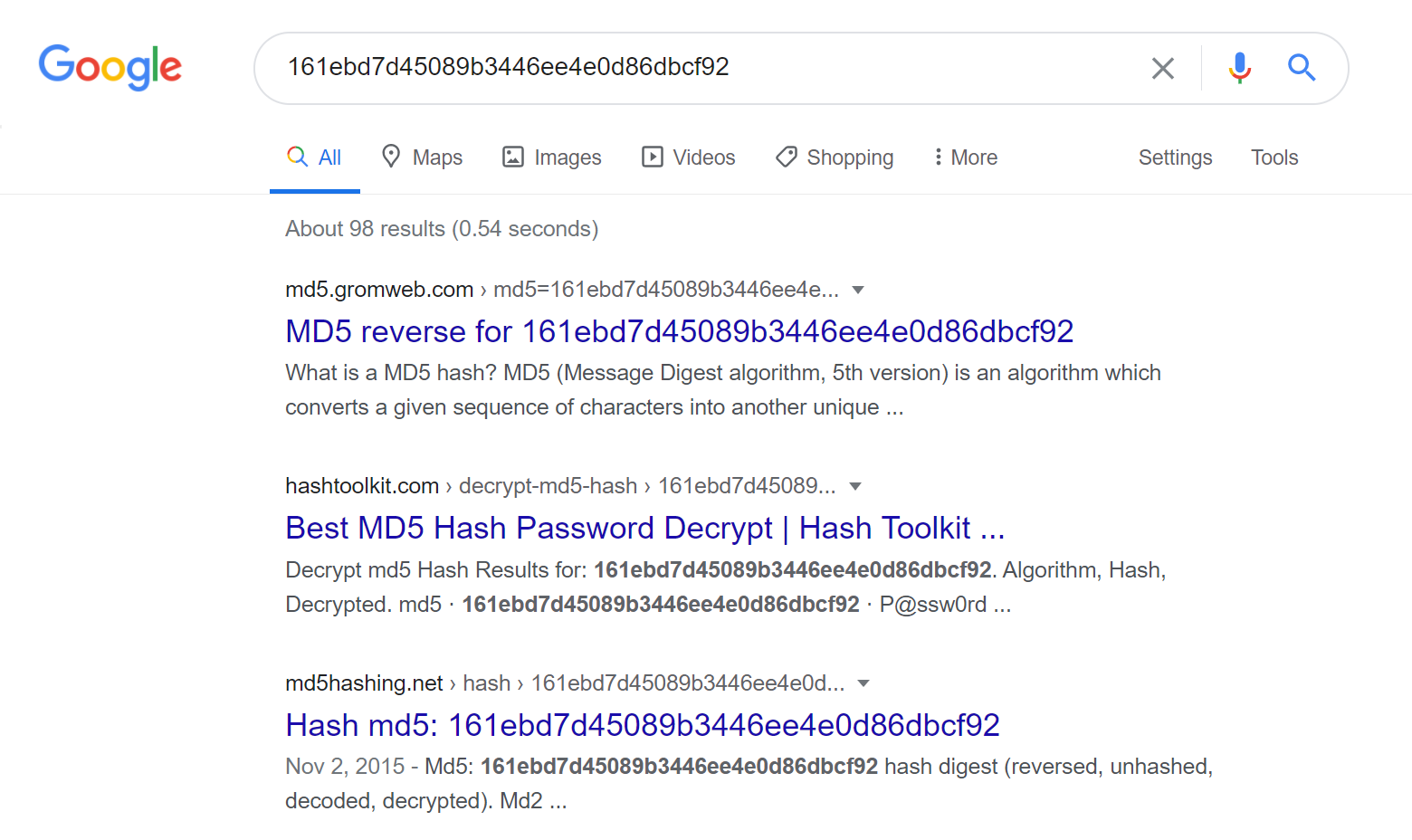
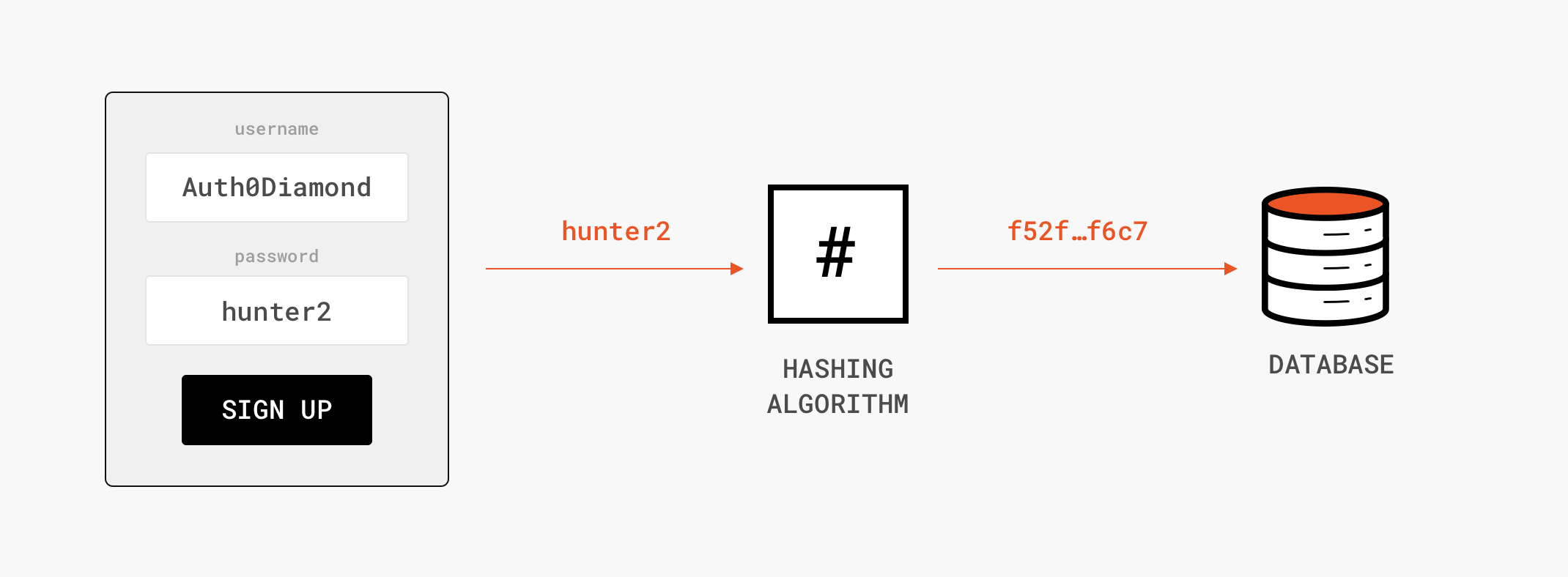
Passwords and hacking: the jargon of hashing, salting and SHA-2 explained | Data and computer security | The Guardian