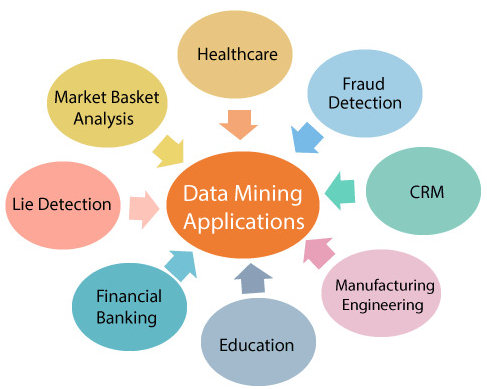
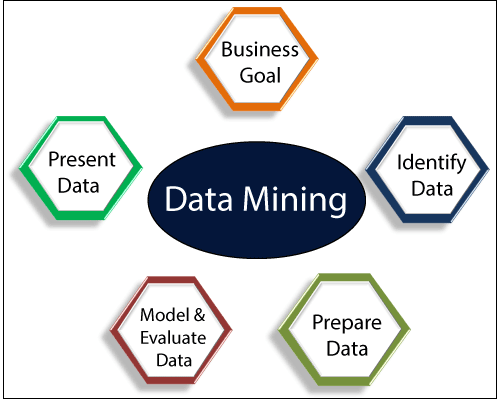
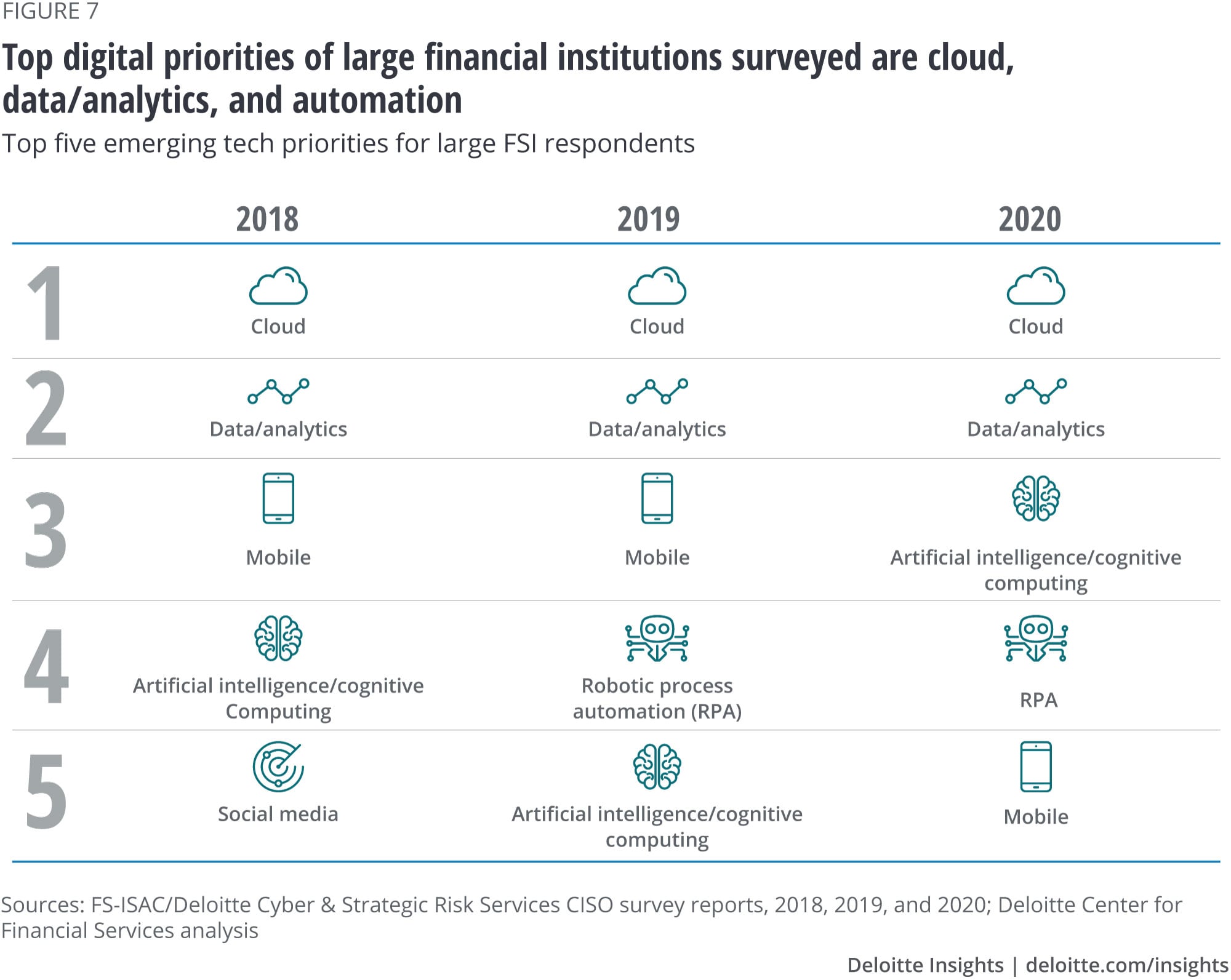
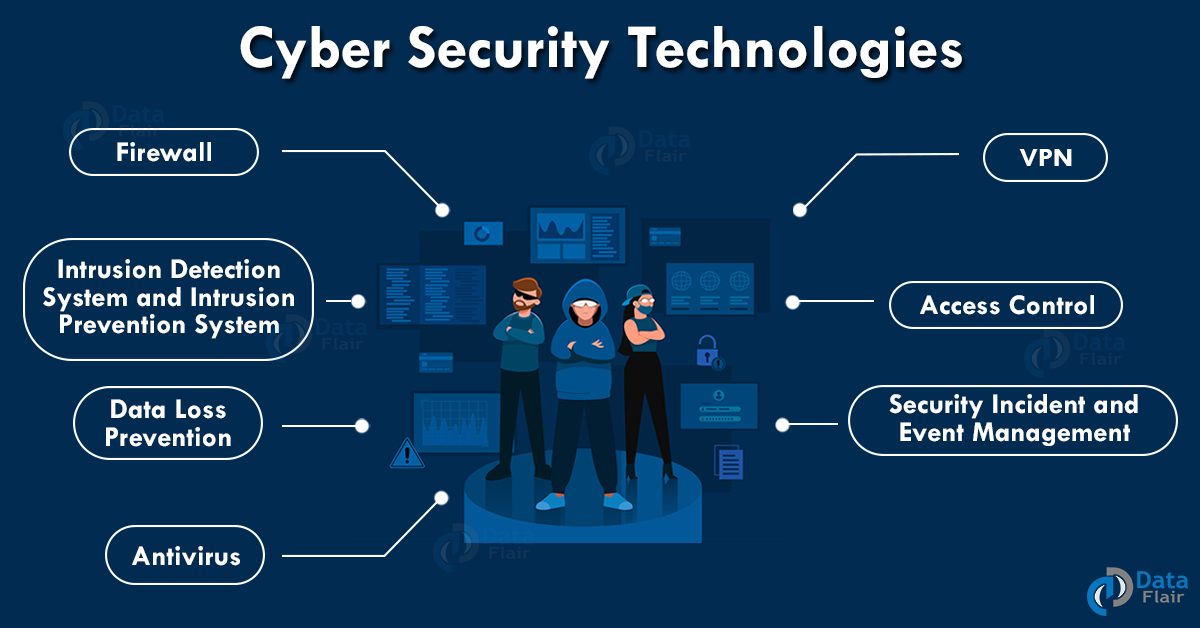
1st day of IEMIS 2020, 2nd International Conference on Emerging Technologies in Data Mining and Information Security - IEM Group

PDF) ************** CALL FOR PAPERS ************** Special Session - Advanced Practices in Cybersecurity and Digital Forensics in IEMIS-2022

Emerging Technologies in Data Mining and Information Security: Proceedings of IEMIS 2020, Volume 2 (Advances in Intelligent Systems and Computing, 1300): Hassanien, Aboul Ella, Bhattacharyya, Siddhartha, Chakrabati, Satyajit, Bhattacharya, Abhishek ...

Emerging Technologies in Data Mining and Information Security: Proceedings of IEMIS 2022, Volume 2 by Paramartha Dutta, Paperback | Barnes & Noble®





:max_bytes(150000):strip_icc()/datamining2-1363d48854c74911aba6c12158135860.png)