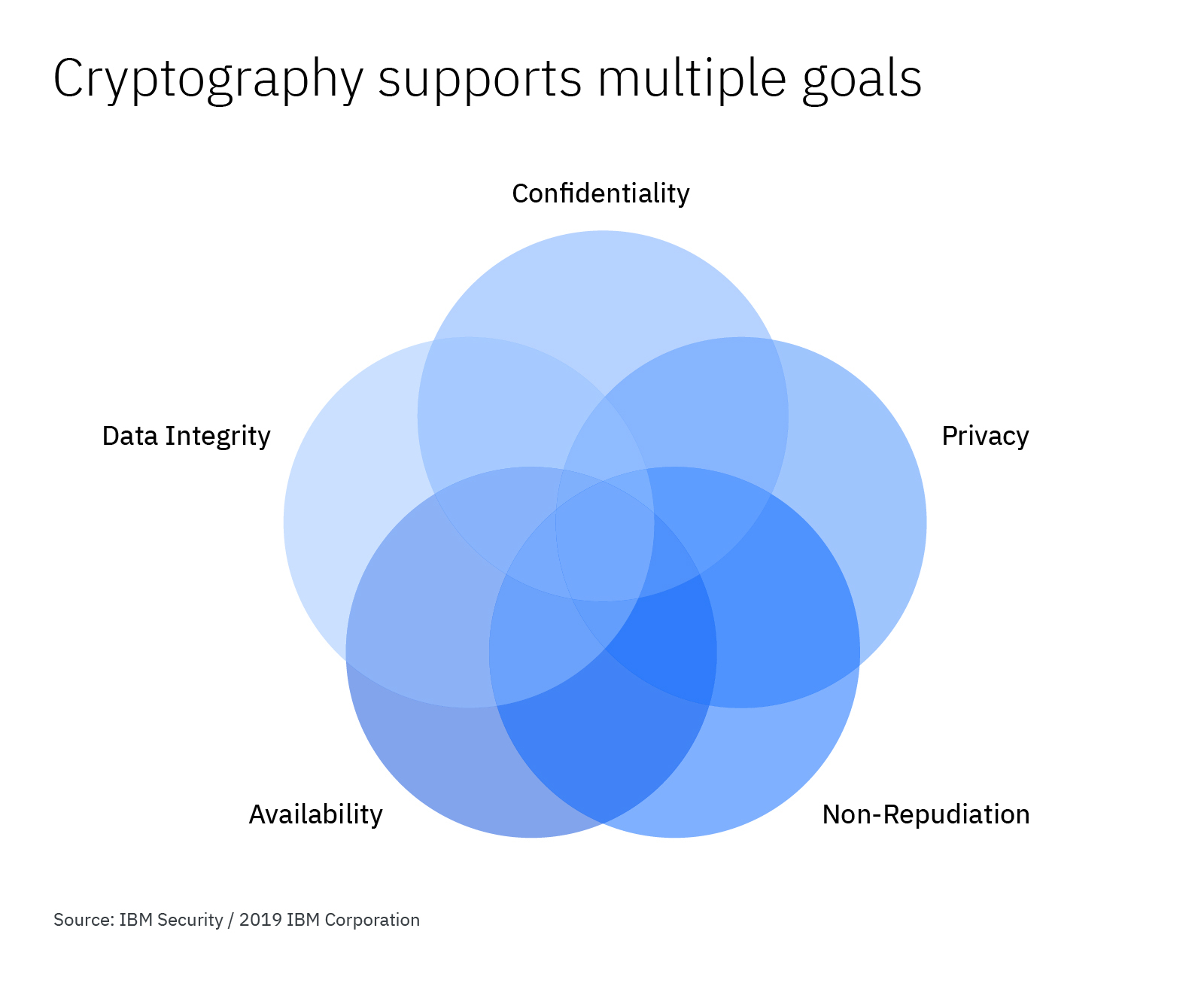
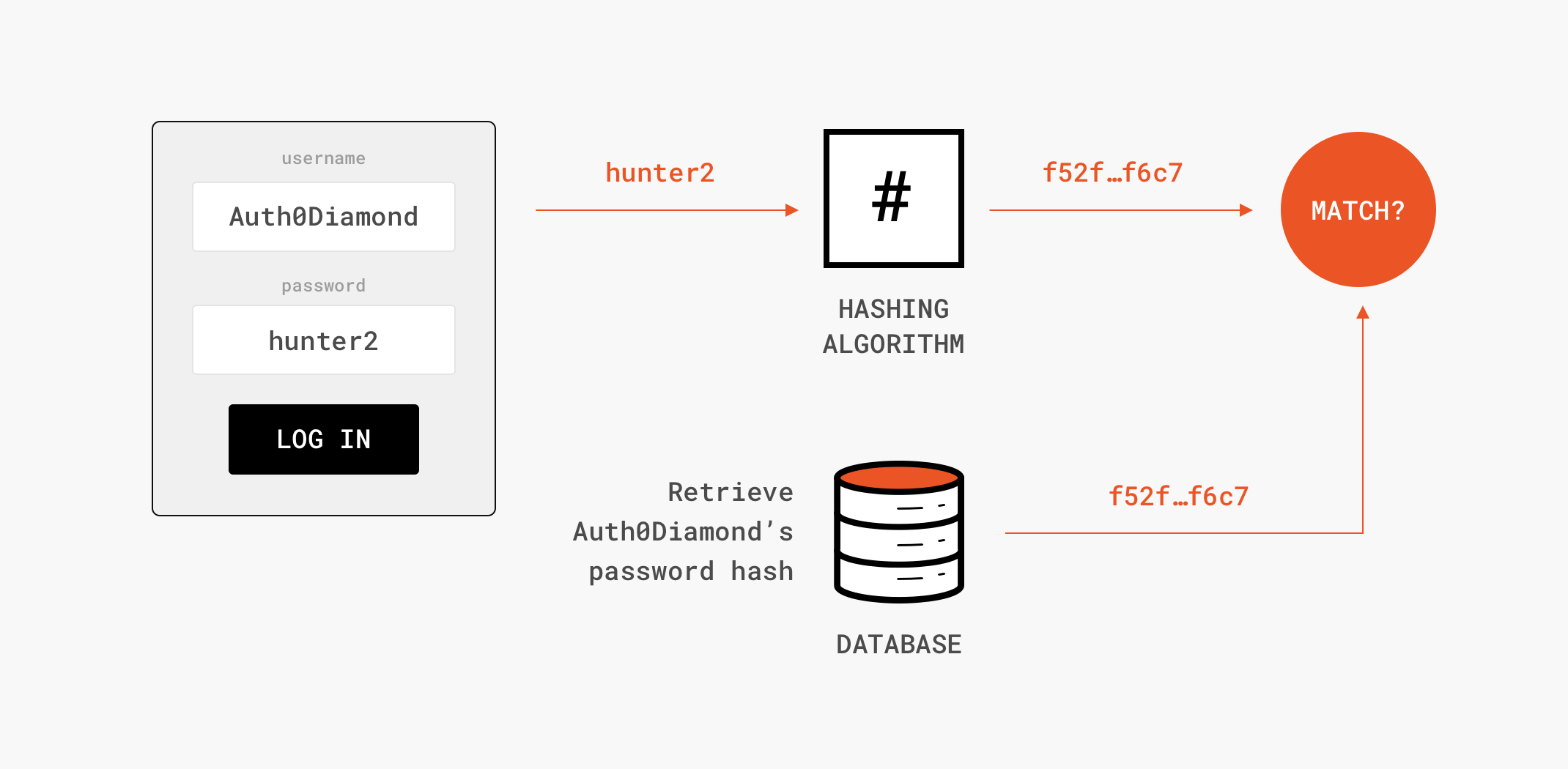
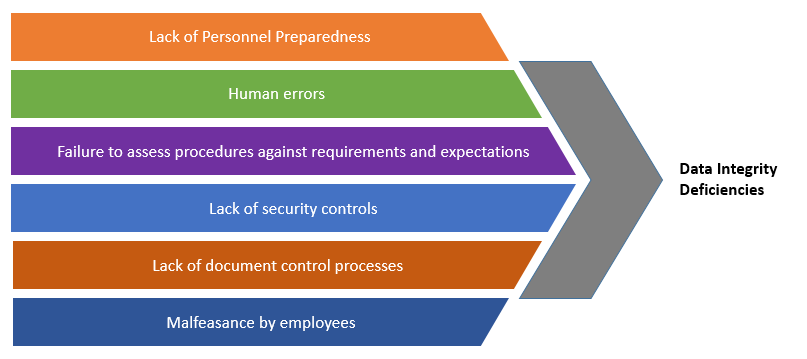
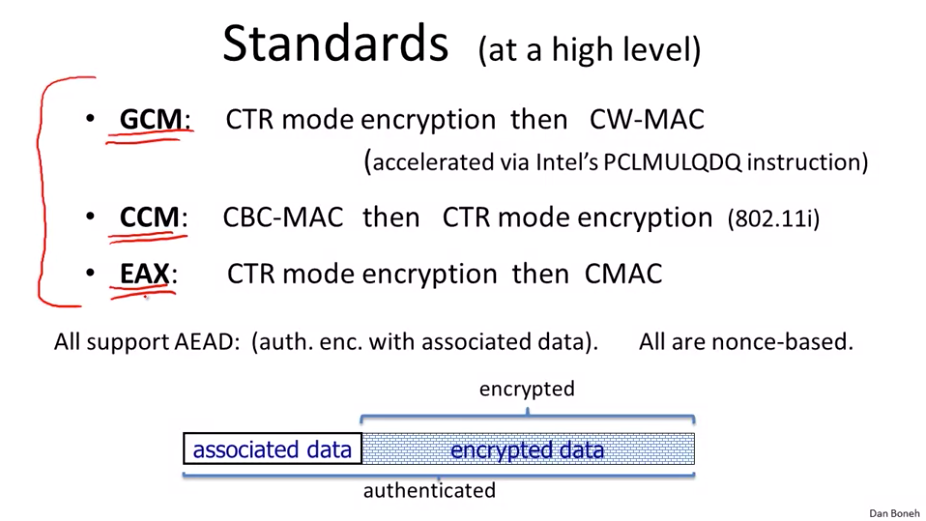
When it Comes to Data Integrity, Can We Just Encrypt the Data? - EngineerZone Spotlight - EZ Blogs - EngineerZone

When it Comes to Data Integrity, Can We Just Encrypt the Data? - EngineerZone Spotlight - EZ Blogs - EngineerZone

Strategy To Be Adopted 1 Data Encryption Overcome The It Security | Presentation Graphics | Presentation PowerPoint Example | Slide Templates