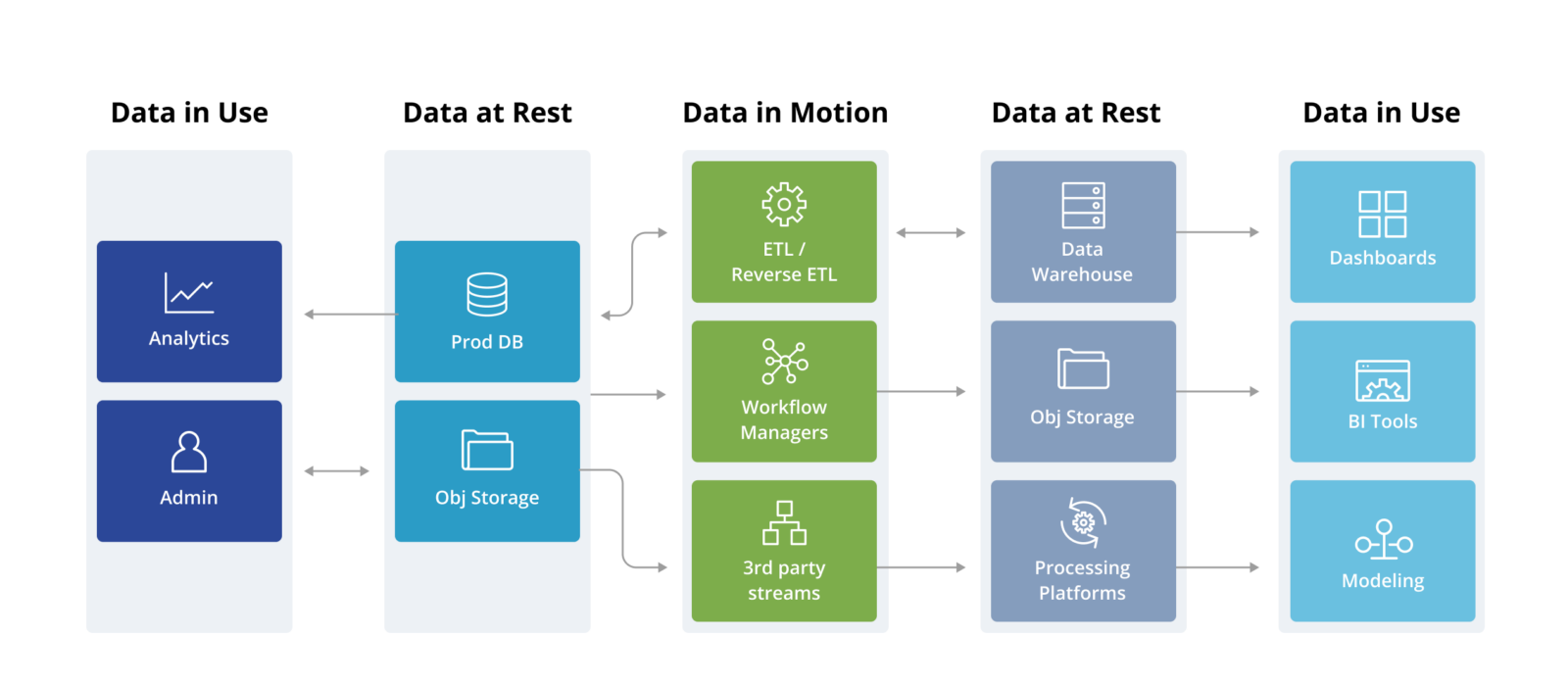
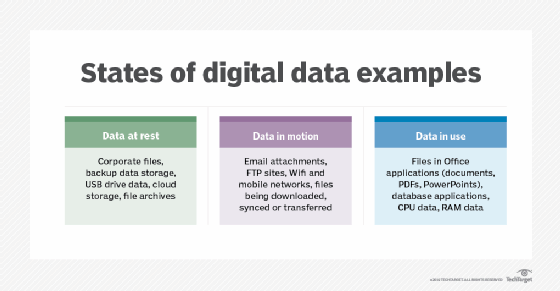
INAP on Twitter: "Infographic: Data at rest vs. data in motion https://t.co/JueVUKRE7R https://t.co/HzkJqwgNH9" / Twitter
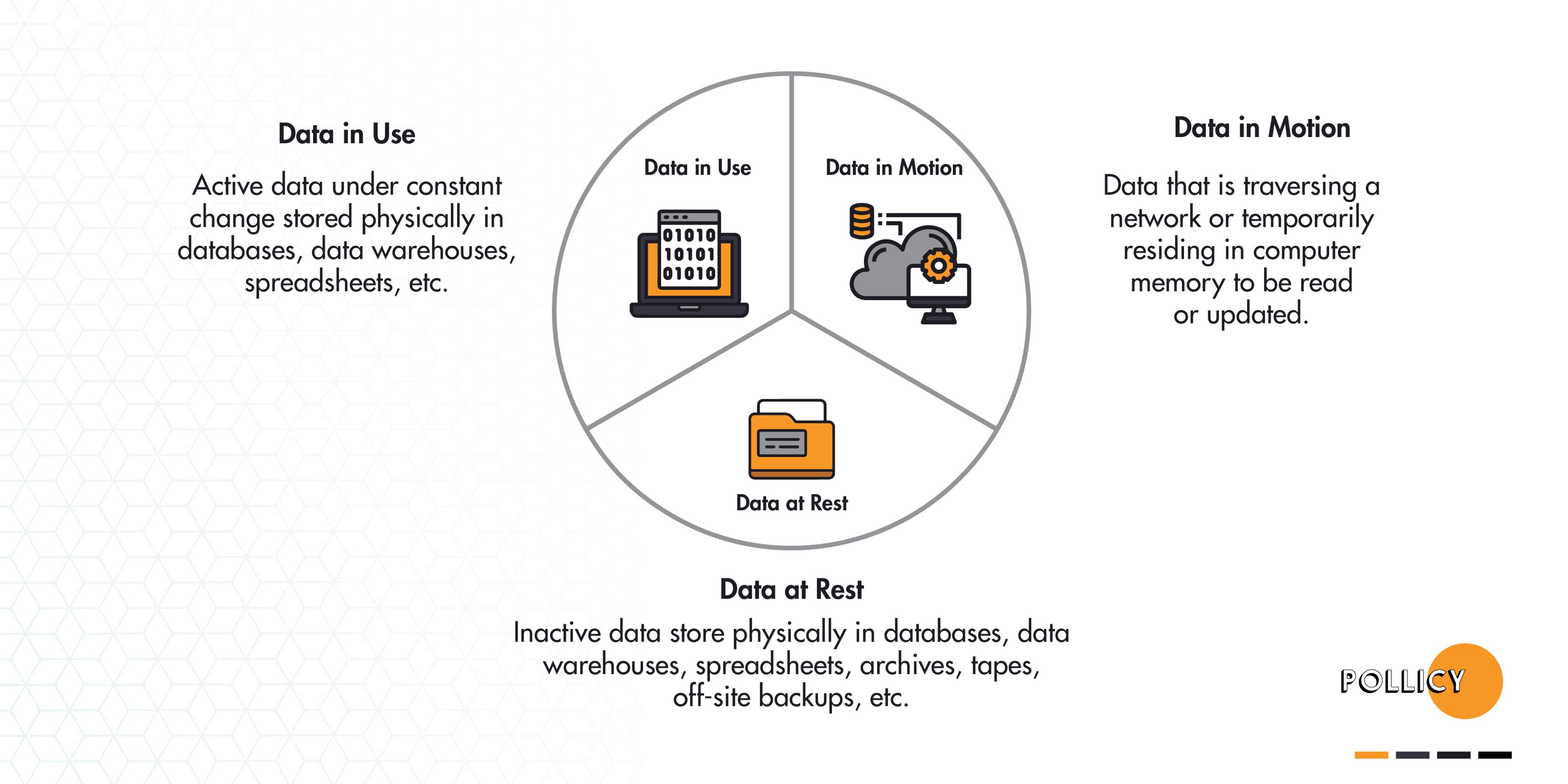
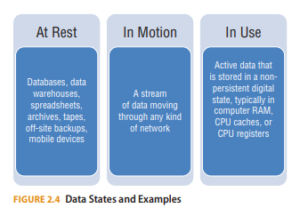
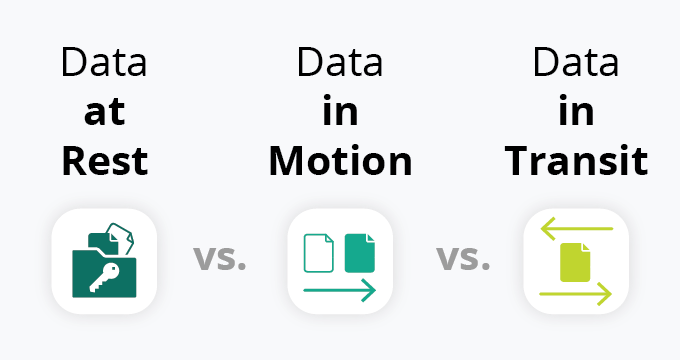
Pollicy Twitter'da: "Understanding the different states digital data can be in can help you select the kinds of security measures and encryption that are appropriate for protecting it. There are three basic
Byte Down: Making Netflix's Data Infrastructure Cost-Effective | by Netflix Technology Blog | Netflix TechBlog